If you’re waiting for the next major cybersecurity breach, history has shown us time and again that you just have to give it a minute. Yahoo. Target. Home Depot. Chase. Sony. OPM. These high profile breaches happen seemingly every few weeks, but the reality is that thousands of cyberattacks are happening every day. It’s no wonder that security is one of the fastest growing sectors in tech.

Even during my time at Symantec a decade ago, it was clear that security was only going to get more important over time. Now, years later, every single one of us has been personally affected by a breach, hack, or cyberattack of some kind. This isn’t going away and it’s not going to stop. Because of this, security software is by far one of the fastest growing parts of the enterprise IT market.
You can imagine that it’s therefore a great time to be a cybersecurity vendor.

At the same time, it’s not all smooth sailing in security land. Because customers are buying so many overlapping solutions, adoption of security technology is a huge challenge. And clients, faced with a growing amount of spend, are asking vendors about the outcomes they are achieving.
As such, security is one of the fastest growing sub-sectors in Customer Success. At Gainsight, we’ve been fortunate to partner with several established, leading, and emerging vendors on their Customer Success strategy—including Cisco, Okta and RiskIQ.
My former boss, Enrique Salem (former CEO of Symantec and now partner at Bain Capital Ventures) and I hosted a dinner with Customer Success leaders at top security companies to discuss what’s unique about the convergence between CS and Security:

The way the attendees saw it, there are three main reasons why cybersecurity is an ideal fit for Customer Success principles and practices—and those same reasons make implementing those principles and practices uniquely difficult, though rewarding.
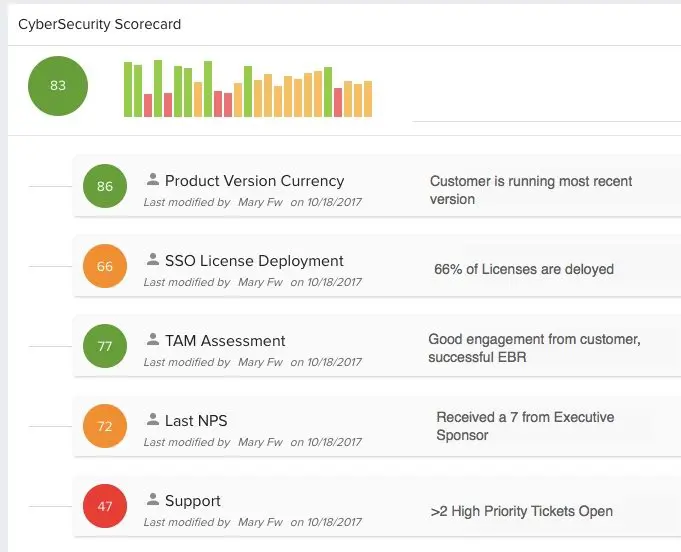
1. Adoption is complex→Make health scores about “currency”
Security tools tend to be different from most softwares in two fundamental ways:
- Users don’t “use” the software.
- “Success” often involves being invisible
In other words, when your security solution is working optimally, you don’t notice it. These companies go to great lengths to make sure their tools are as lightweight and invisible as possible. When you log off at the end of the day and nothing bad happened, that’s a huge win. But from your perspective, it’s just another day.
From a Customer Success Management perspective, that makes tracking health a conundrum. How do you track usage when your product is constantly running in the background? How do you understand satisfaction when your password management app has 100% adoption at a client?
What I learned at this event is that adoption is largely about “currency,” and I don’t mean money. As cybersecurity is about constantly reacting to and preempting threats, how current your version is (in terms of updates and patches) is a huge indicator of how successful you’ll be with the product. In other words, if your customer isn’t up-to-date, they aren’t secure and therefore aren’t getting value.
Customer Success leaders at top security companies have created dynamic health scores that include version currency, breadth of deployment, and other custom factors.
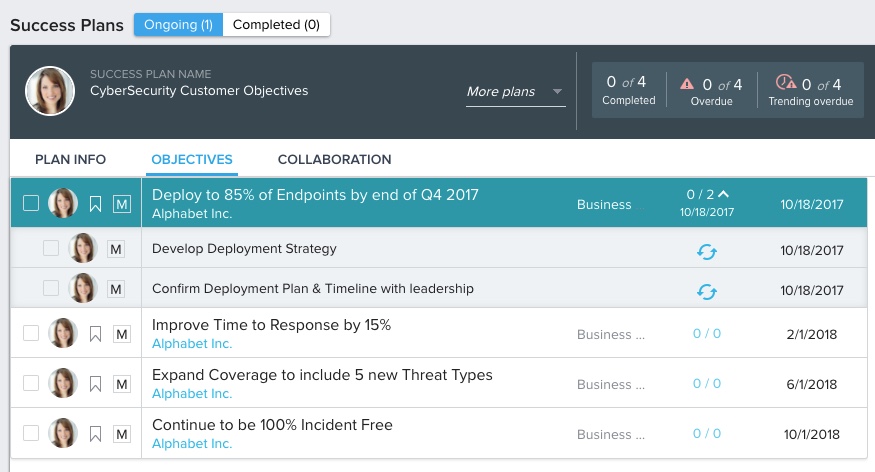
2. Outcomes are difficult to measure→Design end-to-end success plans
As I mentioned before, the customer’s desired outcome with their security solution is (typically) that nothing bad happens and they aren’t disrupted in their day-to-day workflow. To phrase it differently, their objective is a negative, or an absence. For most software products, the goal is much more concrete—and much more positive. For instance, the goal with Gainsight might be a 5x increase in product adoption, or an 8% increase in gross renewals, etc.
With security, how feasible is it to define success as a 0% increase in data breaches? Or to become 10x “more secure.” How do you define that—and more importantly—how do you benchmark that?
Even more challenging is finding the differential impact. If a breach was blocked, which vendor and technology gets credit? If a threat is missed, who takes the blame?
The leaders I talked to see a huge opportunity to better define their customers’ end-to-end success around things like time to detect, time to respond, and the type of threat detected. Building milestones in the customer journey at each stage from pre-sale to Services to Support and Customer Success is critical.
3. Clients are technical→You need technical resources in CSM
At the end of the dinner, we discussed our teams. In every category of Customer Success, companies struggle with the “unicorn” problem. We’d all love CSMs that can do it all—be technical, understand best practices, have walked in the client’s shoes, be firefighters, be strategic, be excellent communicators—and drop some sick karaoke while they’re at it!
In Security, this problem is turbocharged since security buyers are extremely technical.
In the CSM industry broadly, we have witnessed the emergence of a parallel technical partner to the CSM—CS Architect, CS Engineer, Technical Account Manager, etc. And in Security, many companies are leveraging their existing advanced technical resources (e.g., Premium Support Engineers) in this capacity.
If you’re interested in how a Technical Account Management function might look at your company, David Chia from Red Hat wrote a great breakdown of the role here.
There’s more at stake than ARR
At the risk of getting melodramatic, I want to end by underscoring the importance of Customer Success beyond the basic economic value proposition that we (understandably) tend to focus on in B2B software. We know that when customers are successful, vendors are successful—it’s the founding premise of my company. But when it comes to Security, we don’t need that conditional statement to understand just how critical an industry it is.
When Security customers are successful, their data is safe. My data is safe. My kids’ data. That’s a heavy burden for companies that so often tend to themselves “run in the background” in the public consciousness. If you’re reading this and you’re in Security, my deepest thanks for what you do. Here’s to keeping all of us successful—and safe.
If you want to see how one of our customers, RiskIQ, is using Gainsight to help keep their clients successful, take a look at this case study and testimonial video.

